Get-MgAuditLogSignIn: How to Monitor Sign-In Activities in Microsoft 365
This guide explains how to use Get-MgAuditLogSignIn in Graph PowerShell to retrieve sign-in logs from Azure AD. Learn how to query logs for specific users, filter by sign-in status, and export data for auditing purposes.
The Get-MgAuditLogSignIn cmdlet retrieves sign-in activities in the Microsoft 365 environment. This is useful for monitoring and auditing user sign-ins, which helps in maintaining security and compliance.
Prerequisites
- You should install Microsoft Graph PowerShell module by running Install-Module Microsoft.Graph -Scope CurrentUser command.
- You should connect to Microsoft Graph PowerShell module by running Connect-MgGraph -Scopes "AuditLog.Read.All".
- To execute Find-GraphMgPermission cmdlet, you need 'AuditLog.Read.All, Directory.Read.All, Directory.ReadWrite.All' Graph API permissions. These permissions could be either delegated or application level permission. Note: In most cases, AuditLog.Read.All is sufficient for retrieving sign-in activities. However, depending on your specific scenario or if the cmdlet's behavior depends on directory data, additional permissions like Directory.Read.All might be required
Basic Syntax
Here’s the basic syntax of the Get-MgAuditLogSignIn: Get-MgAuditLogSignIn [-Top <Int32>
] [-Filter < String >
] [-Select <String >
] [-ExpandProperty <String >
] [-ConsistencyLevel < ConsistencyLevel >
] [<CommonParameters >
]
Key Parameters:
- -Top <Int32> Specifies the maximum number of records to retrieve. Useful for limiting the output to a manageable size, especially when dealing with large data sets.
- -Filter <String>: Applies an OData query to filter the results based on specific criteria. Allows you to narrow down the results to specific sign-in activities, such as those for a particular user or within a certain date range.
- -Select <String>: Specifies a comma-separated list of properties to include in the response. Helps in focusing on specific properties of the sign-in activities, making the output more readable and relevant to your needs.
- <Common Parameters>: The Get-MgAuditLogSignIn cmdlet supports common parameters that are available in many PowerShell cmdlets. These include -Verbose, -Debug, -ErrorAction, -ErrorVariable, -OutBuffer, and -OutVariable.
Retrieve Top 10 Sign-In Activities
This command retrieves the top 10 most recent sign-in activities.
Retrive Sign-In Activity Based On Specific ID
Since every user sign-in event has a ID, you can also retrieve detailed information about the specific sign-in event by passing its ID.
Note: The sign-in event ID can be obtained by executing Get-MgAuditLogSignIn cmdlet.
Audit Sign-In Activity for the Past 30 Days
Here's a Graph PowerShell script that audits the user sign-in activity for the past 30 days using the Get-MgAuditLogSignIn cmdlet.
- $startDate is set to 30 days from today.
- The $startDate is passed to Get-MgAuditLogSignIn cmdlet as the value for createdDateTime parameter. The results are saved in $signIns parameter.
- The UserPrincipalName, CreatedDateTime, IpAddress, Location and Status are pulled from $signIns parameter and displayed.
Cmdlet Tips
- Use Pagination for Large Datasets:
- Tip: When retrieving sign-in activity for a large number of users or over an extended period, use pagination (-Top parameter) to avoid overwhelming the system or missing data.
- Example: $logs = Get-MgAuditLogSignIn -Top 100
- Filter Sign-Ins by Date Range for Faster Results:
- Tip: Use the -Filter parameter to limit sign-in records to a specific date range, improving the performance of your query and ensuring that only relevant data is retrieved.
- Example: Get-MgAuditLogSignIn -Filter "createdDateTime ge 2024-01-01 and createdDateTime le 2024-08-01"
Use Cases
- Monitoring Suspicious Sign-In Activities:
- Scenario: Detecting unusual sign-in patterns (e.g., multiple failed attempts or sign-ins from unexpected locations) is critical for security teams.
- Implementation: Use Get-MgAuditLogSignIn to retrieve and export sign-in data, ensuring that all login events are tracked for auditing purposes.
- Benefit: Simplifies the generation of compliance reports, ensuring that all necessary access logs are available for review.
- Compliance Reporting for Sign-In Activities:
- Scenario: Organizations must often generate compliance reports showing user access to critical systems over a defined period.
- Implementation: Use Get-MgAuditLogSignIn to filter and identify sign-in attempts that may indicate a compromised account.
- Benefit: Helps improve security posture by proactively identifying and addressing potential threats.
- Analyzing User Sign-In Trends:
- Scenario: Organizations may want to understand when and how frequently users are accessing systems.
- Implementation: Use Get-MgAuditLogSignIn to gather and analyze user sign-in patterns, such as peak usage times or common sign-in locations.
- Benefit: Helps optimize resource allocation by identifying busy periods, which can assist in adjusting infrastructure or capacity.
- Identifying Stale Accounts:
- Scenario: User accounts that have not signed in for a long time may be inactive and pose a security risk.
- Implementation: Use Get-MgAuditLogSignIn to filter out users who haven’t signed in for a specific period, helping administrators review inactive accounts.
- Benefit: Streamlines the process of identifying stale or unused accounts that can be removed or deactivated to maintain security.
Possible Errors You Might Face
Here are some best practices you can follow while using Get-MgAuditLogSignIn cmdlet:
-
Insufficient Permissions to Access Sign-In Logs: Attempting to retrieve sign-in logs may fail if the account running the cmdlet does not have sufficient permissions. AuditLog.Read.All or Directory.Read.All are the required Graph API permissions.
- Invalid Filter Syntax error: Check the syntax of your filter query. Ensure it follows the OData query standards. For example, use eq for equality and ensure the property names are correct.
- Sign-In Activity Data is Incomplete: The cmdlet may return incomplete sign-in activity if there are too many records or filtering criteria are not properly defined. Use pagination (-Top parameter) and specific query filters (e.g., date range or specific users) to retrieve the full set of sign-in data in batches.
Note: Always refer to Get-MgAuditLogSignIn Microsoft Graph PowerShell Documentation to stay updated about the cmdlet.
Frequently Asked Questions
- What is Get-MgAuditLogSignIn used for?
- How can I retrieve sign-in logs for a specific user?
Get-MgAuditLogSignIn is a Microsoft Graph PowerShell cmdlet used to retrieve Azure AD sign-in logs. It is commonly used for monitoring user activities, detecting failed logins, and auditing security events.
Use the -Filter parameter to query logs for a specific user’s sign-in activity. For example:
Get-MgAuditLogSignIn -Filter "userPrincipalName eq 'user@domain.com'" -AllYes, you can filter logs by sign-in status using the -Filter parameter. For example:
Get-MgAuditLogSignIn -Filter "status/errorCode ne 0" -AllYou can export sign-in logs for further analysis using this script:
$SignInLogs = Get-MgAuditLogSignIn -All
$SignInLogs | Select-Object UserPrincipalName, IpAddress, Status, CreatedDateTime | Export-Csv -Path "C:\Path\To\SignInLogs.csv" -NoTypeInformation
Get Sign In Audit Logs Using Microsoft Entra Admin Center (formerly Azure AD Admin Center)
- Login into Microsoft 365 Admin Center
- Select Identity (Microsoft Entra Admin Center) from Admin Centers
- In the Microsoft Entra Admin Center that opens up, select Identity >> Monitoring & Health >> Sign-in Logs
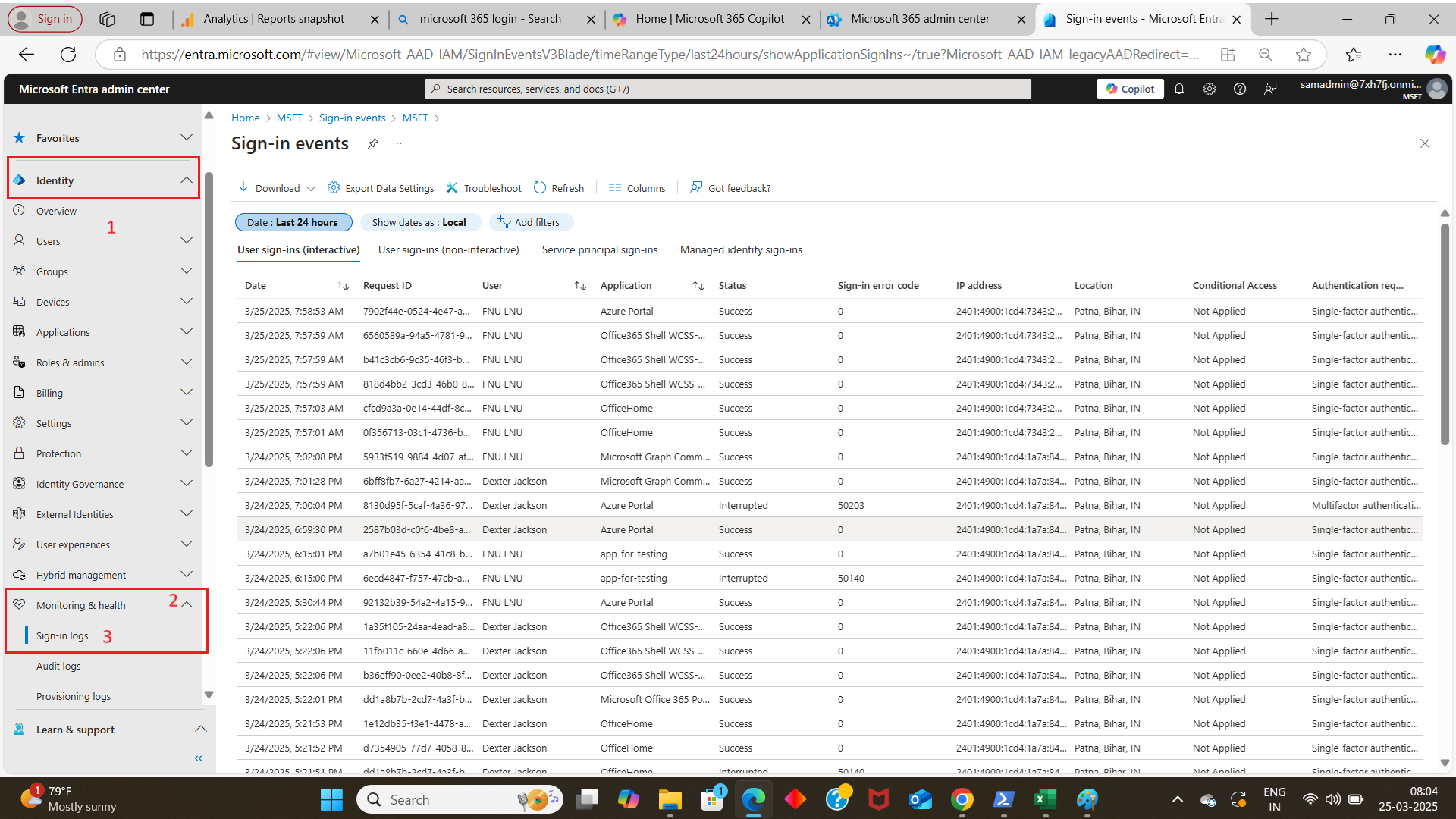
The
Get-MgAuditLogSignIn cmdlet fetches sign-in logs from Microsoft Entra (Azure AD), which are only available to tenants with Azure AD Premium P1 or P2 licensing.Without the appropriate license, the cmdlet will return empty results or access denied errors.
When filtering sign-in logs using
createdDateTime, always use the ISO 8601 format (e.g., "2024-06-01T00:00:00Z").Using incorrect formats will lead to empty results or query errors.
Conclusion:
Understanding the detailed syntax of the Get-MgAuditLogSignIn cmdlet allows you to effectively retrieve and filter sign-in activities in Microsoft 365. Each parameter provides a specific function that enhances the cmdlet's flexibility and usability, enabling you to tailor your queries to your exact requirements.
If You Prefer the Graph API Way
Note: Microsoft Entra sign-in logs are accessible via the /auditLogs/signIns endpoint. Use $top, $filter, and $orderby to control results, and ensure proper ISO 8601 datetime format when filtering by date.
- Retrieve Top 10 Sign-In Activities
- Retrieve a Specific Sign-In Record by ID
- Audit Sign-In Activity for the Past 30 Days
$uri = "https://graph.microsoft.com/v1.0/auditLogs/signIns?`$top=10"
$response = Invoke-MgGraphRequest -Method GET -Uri $uri
if ($response.value) {
foreach ($signIn in $response.value) {
Write-Output "User : $($signIn.userDisplayName)"
Write-Output "Status : $($signIn.status.errorCode)"
Write-Output "Time : $($signIn.createdDateTime)"
Write-Output "App : $($signIn.appDisplayName)"
Write-Output "`n"
}
} else {
Write-Output "No sign-in records found."
}
💡 You can also sort results using $orderby=createdDateTime desc to get the latest first.
# Replace with actual sign-in ID
$signInId = "5c572ba9-9b20-495f-a4e0-b3d058da8f02"
$uri = "https://graph.microsoft.com/v1.0/auditLogs/signIns/$signInId"
$response = Invoke-MgGraphRequest -Method GET -Uri $uri
if ($response) {
Write-Output "User : $($response.userDisplayName)"
Write-Output "User ID : $($response.userId)"
Write-Output "IP Address : $($response.ipAddress)"
Write-Output "Status Code : $($response.status.errorCode)"
Write-Output "App : $($response.appDisplayName)"
} else {
Write-Output "Sign-in record not found."
}
🔐 The sign-in ID must be a valid GUID from existing log entries.
# Filter sign-ins for the past 30 days based on createdDateTime
$startDate = (Get-Date).AddDays(-30).ToString("yyyy-MM-ddTHH:mm:ssZ")
$filter = "`$filter=createdDateTime ge $startDate"
$uri = "https://graph.microsoft.com/v1.0/auditLogs/signIns?$filter"
$response = Invoke-MgGraphRequest -Method GET -Uri $uri
if ($response.value) {
foreach ($entry in $response.value) {
Write-Output "User : $($entry.userDisplayName)"
Write-Output "Time : $($entry.createdDateTime)"
Write-Output "Status Code : $($entry.status.errorCode)"
Write-Output "`n"
}
} else {
Write-Output "No sign-in activity in the last 30 days."
}
📌 The date format must be in ISO 8601 format (yyyy-MM-ddTHH:mm:ssZ). UTC is recommended.
Required Permissions
You must have one of the following:
AuditLog.Read.AllDirectory.Read.All(read-only user + sign-in data)
Graph API Documentation
👉 GET /auditLogs/signIns - Microsoft Graph v1.0
Related Articles:
Using Get-MgDirectoryRole in Graph PowerShellUsing Get-MgUserLicenseDetail in Graph PowerShell
Using Find-GraphMgCommand in Graph PowerShell
Connect to Microsoft 365 Using PowerShell
How to Create Bulk Users in Office 365 Using Graph PowerShell?
Create Microsoft 365 Group Using Microsoft Graph PowerShell
Block Microsoft 365 User Using Microsoft Graph PowerShell
Assign Microsoft 365 License Using Graph PowerShell
Microsoft 365 User Management Using Graph PowerShell
Checking Group Membership in Microsoft 365
Bulk Assign Microsoft 365 License
Find Inactive Users in Microsoft 365
Using Powershell Graph Search Query
Using Powershell Graph Filter Query
Using Where-Object In Graph PowerShell
Using Expand Property In Graph PowerShell
Using Select Object In Graph PowerShell
Using -Contains Operator In Graph PowerShell
Add User to Multiple Microsoft 365 Groups Using Graph PowerShell
Get Microsoft 365 User Location Using Graph PowerShell
Import Microsoft 365 Groups from CSV File Using Graph PowerShell
Microsoft 365 Group User Import Using Graph PowerShell