Retrieve Successful User Logins Using Graph PowerShell
Tracking successful user sign-ins is vital for monitoring user activity, auditing sign-in patterns, and ensuring secure access to Microsoft 365 services. This article walks you through a basic Graph PowerShell script to extract successful user login data using the Microsoft Graph PowerShell SDK (v1.0), with enhancements and troubleshooting guidance.
Script – Fetch Successful User Logins
# Connect to Microsoft Graph with necessary permissions
Connect-MgGraph -Scopes "AuditLog.Read.All"
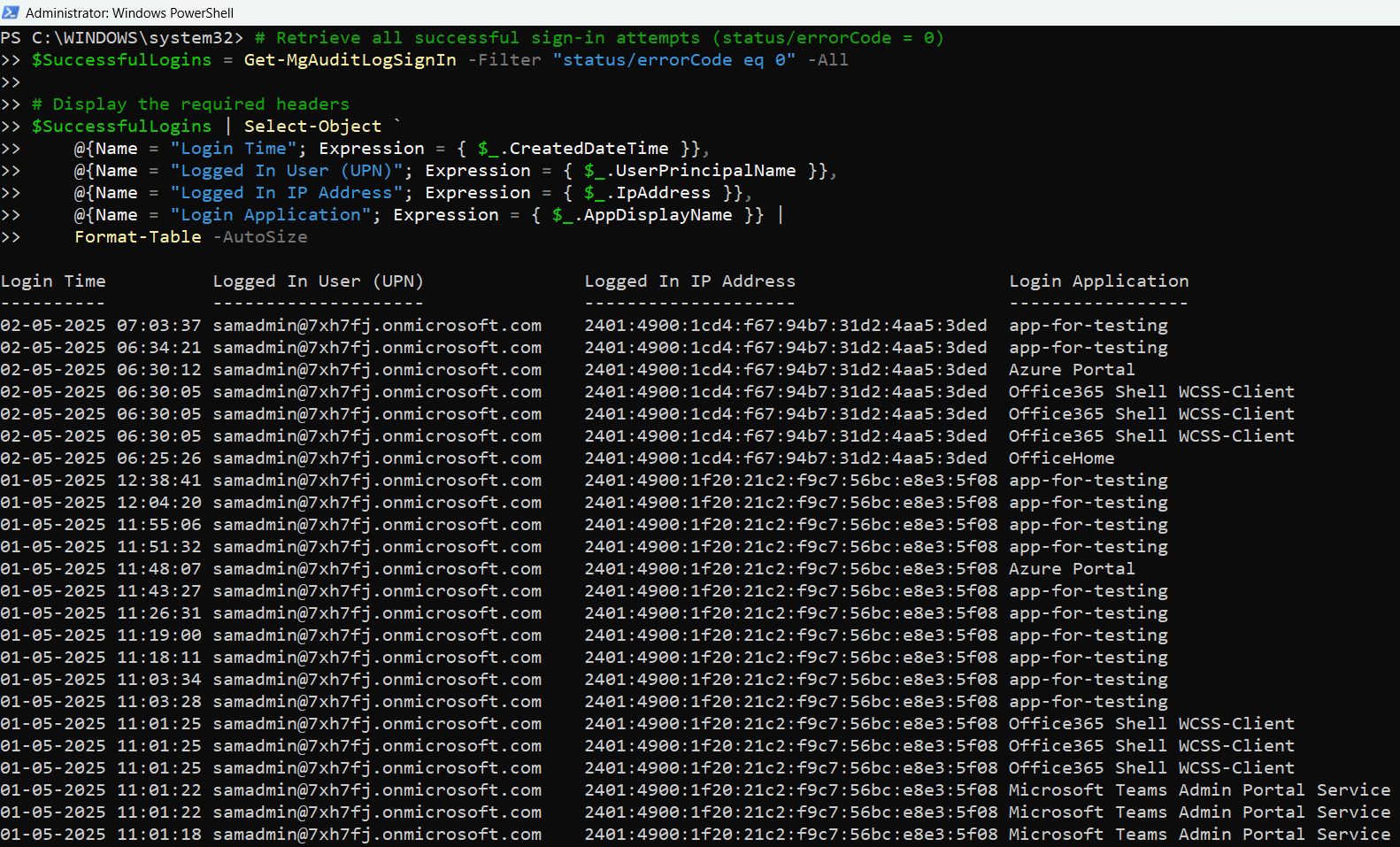
# Retrieve all successful sign-in attempts (status/errorCode = 0)
$SuccessfulLogins = Get-MgAuditLogSignIn -Filter "status/errorCode eq 0" -All
# Display the required headers in the PowerShell console
$SuccessfulLogins | Select-Object `
@{Name = "Login Time"; Expression = { $_.CreatedDateTime }},
@{Name = "Logged In User (UPN)"; Expression = { $_.UserPrincipalName }},
@{Name = "Logged In IP Address"; Expression = { $_.IpAddress }},
@{Name = "Login Application"; Expression = { $_.AppDisplayName }} |
Format-Table -AutoSize
How the Script Works
- Authentication: The script initiates a connection to Microsoft Graph using Connect-MgGraph and requests the AuditLog.Read.All permission scope.
- Data Retrieval: It uses the Get-MgAuditLogSignIn cmdlet to fetch sign-in logs. The filter status/errorCode eq 0 ensures that only successful logins are retrieved.
- Output Formatting: Using Select-Object, the script picks the following fields:
- Login Time: Timestamp of the successful sign-in
- UserPrincipalName: The UPN (email) of the signed-in user
- IP Address: Source IP from which the user signed in
- Application: The app or service used during the sign-in attempt
- Result Presentation: The data is neatly rendered in a formatted table using Format-Table.
Further Enhancements
Here are some enhancements you can apply to tailor the script to your needs:
Filter by Date Range
To focus on recent activity, you can filter results to include only those in the last 7 days:
$Since = (Get-Date).AddDays(-7)
$RecentSuccessLogins = $SuccessfulLogins | Where-Object { $_.CreatedDateTime -ge $Since }
Export to CSV
Exporting to a .csv file is helpful for audits and sharing reports:
$SuccessfulLogins | Select-Object ... | Export-Csv -Path ".\SuccessfulLogins.csv" -NoTypeInformationFilter by User or Application
You can further narrow results by specific user or application:
$SuccessfulLogins | Where-Object { $_.UserPrincipalName -eq "jane.doe@domain.com" }Possible Errors & Solutions
| Error | Cause | Solution |
| Connect-MgGraph is not recognized | Microsoft Graph SDK is not installed | Run Install-Module Microsoft.Graph -Scope CurrentUser |
| Access Denied or Insufficient privileges | Missing admin consent or permission | Ensure AuditLog.Read.All is granted and consented by an admin |
| status/errorCode is not valid | Incorrect OData filter syntax | Use status/errorCode eq 0 (note case-sensitivity and exact path) |
Use Cases
- User Activity Audits: Track when users successfully log into the tenant.
- Application Usage Insights: See which applications users are accessing.
- IP Address Auditing: Identify the geographical source of sign-ins.
- Compliance Reporting: Export successful login history for internal or external compliance.
-Top with -All for Large Log RetrievalsWhen querying sign-in logs over long periods, data volumes can be huge. Combining
-All with a smaller -Top (e.g. -Top 1000) helps manage pagination and API load while ensuring you fetch all records without overwhelming the session.
ipAddress to Detect Unusual Sign-In SourcesCollecting the
ipAddress field (e.g., in your Select-Object) can help pinpoint sign-ins from unexpected locations.
Exporting this data supports security audits and can highlight potentially unauthorized or suspicious access.
Conclusion
With just a few lines of PowerShell, you can retrieve valuable insight into successful user sign-ins across your Microsoft 365 environment. This script is an excellent starting point for building robust sign-in activity reports that enhance your auditing, security monitoring, and compliance workflows.