Track Disabled User Accounts in Microsoft 365 Using Graph PowerShell
Disabling user accounts in Microsoft 365 is a common administrative action — typically triggered when employees leave the organization, accounts are compromised, or temporarily deactivated for compliance. But who performed the disable action? When? And was it successful?
In this article, we’ll show you how to use Microsoft Graph PowerShell to retrieve all “Disable account” audit logs and track this crucial activity across your tenant.
The Script
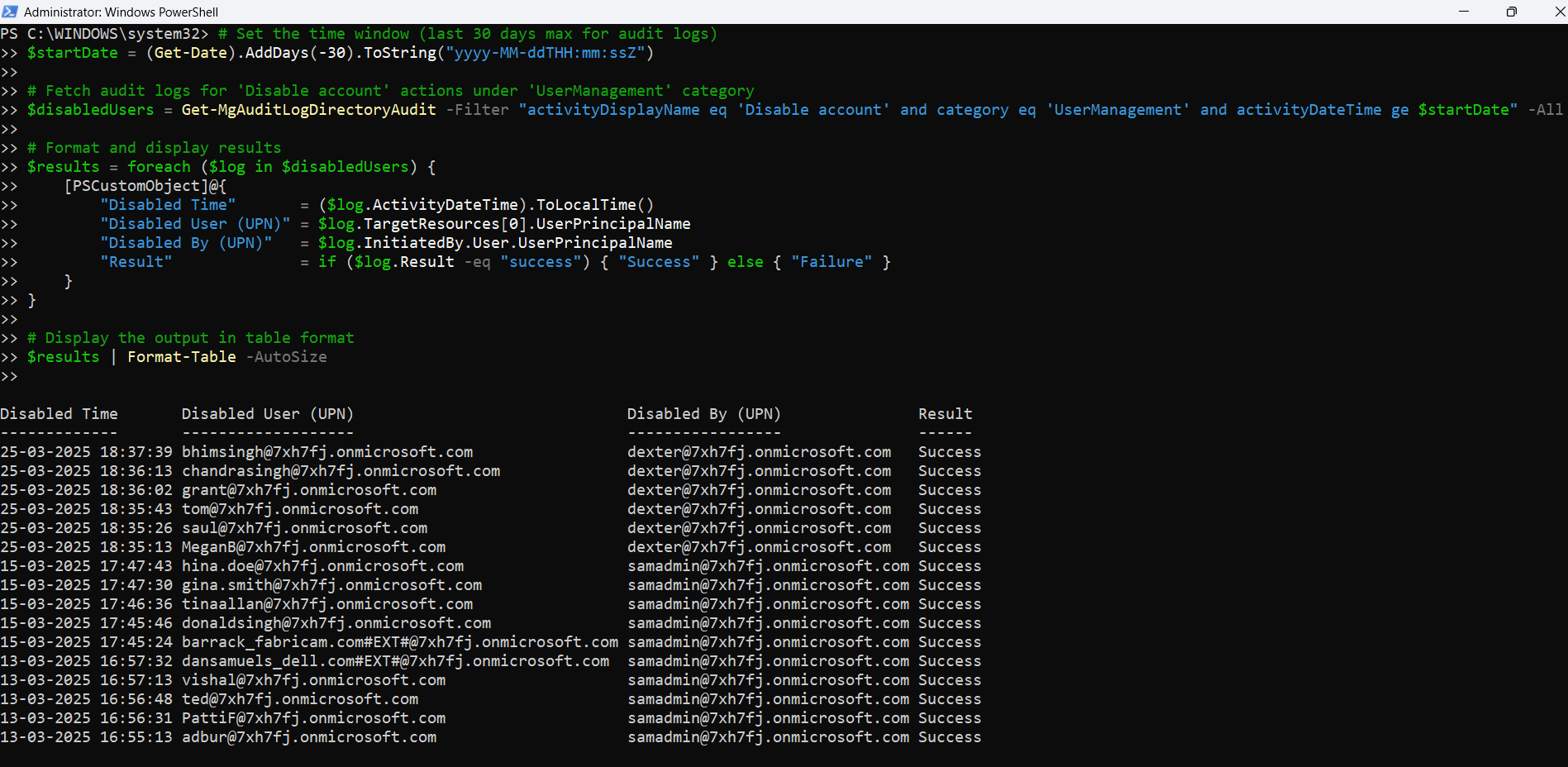
# Connect to Microsoft Graph with required scopes
Connect-MgGraph -Scopes "AuditLog.Read.All", "User.Read.All"
# Set the time window (last 30 days max for audit logs)
$startDate = (Get-Date).AddDays(-30).ToString("yyyy-MM-ddTHH:mm:ssZ")
# Fetch audit logs for 'Disable account' actions under 'UserManagement' category
$disabledUsers = Get-MgAuditLogDirectoryAudit -Filter "activityDisplayName eq 'Disable account' and category eq 'UserManagement' and activityDateTime ge $startDate" -All
# Format and display results
$results = foreach ($log in $disabledUsers) {
[PSCustomObject]@{
"Disabled Time" = ($log.ActivityDateTime).ToLocalTime()
"Disabled User (UPN)" = $log.TargetResources[0].UserPrincipalName
"Disabled By (UPN)" = $log.InitiatedBy.User.UserPrincipalName
"Result" = if ($log.Result -eq "success") { "Success" } else { "Failure" }
}
}
# Display the output in table format
$results | Format-Table -AutoSize
How the Script Works
This PowerShell script is built on top of the Microsoft Graph API and performs the following actions:
- Connects to Graph API with the following delegated permissions:
- AuditLog.Read.All
- User.Read.All
- Sets a date filter to retrieve audit logs from the last 30 days — the maximum window supported by Graph API for audit logs.
- Filters the audit logs to specifically target:
- activityDisplayName eq 'Disable account'
- category eq 'UserManagement'
- Extracts and formats the log details to display:
- Disabled Time
- Disabled User (UPN)
- Disabled By (UPN)
- Result (Success or Failure)
- Outputs the results in a clean, readable table format using Format-Table.
Further Enhancements
Want to take it to the next level? Here are a few enhancements you can add:
- Export to CSV
$results | Export-Csv -Path "DisabledUsersReport.csv" -NoTypeInformationPerfect for offline review or record-keeping.
$results | Where-Object { $_."Disabled By (UPN)" -like "*admin.contoso.com" }Helpful when auditing actions performed by a specific individual.
Use Cases
- Security & Compliance Monitoring: Ensure all account disable actions are logged and attributed.
- Offboarding Validation:Cross-check that all departing employees’ accounts were properly disabled.
- Suspicious Behavior Investigation: Track any abnormal disabling of active user accounts.
- Automated Reporting: Integrate with automation platforms to generate regular audit reports.
Possible Errors & Solutions
| Error | Cause | Solution |
| Access Denied | Missing required Graph permissions | Use Connect-MgGraph -Scopes "AuditLog.Read.All", "User.Read.All" |
| No data returned | No disable actions in the last 30 days | Confirm recent account disable activity exists in the tenant |
| TargetResources[0].UserPrincipalName is null | Log object is missing expected properties | Add null checks or fallback to DisplayName |
| CommandNotFoundException | Graph module not installed | Run: Install-Module Microsoft.Graph -Scope CurrentUser |
Conclusion
Tracking account disable actions is critical for visibility, compliance, and operational accountability in Microsoft 365. This Graph PowerShell script gives you a clear and concise way to see who disabled which user, when, and whether the action succeeded — all within seconds.
This script can be scheduled, enhanced, or integrated into broader security workflows, making it a must-have for every Microsoft 365 administrator.