Track "Delete Group" Events in Microsoft 365 using Graph PowerShell
Monitoring group deletion activities is vital to maintaining control over your Microsoft 365 environment. Whether groups are deleted intentionally or accidentally, having an audit trail ensures that IT admins can review and take corrective action if necessary.
In this article, we’ll walk through a Graph PowerShell script that fetches "Delete group" events under the GroupManagement category, showing exactly when a group was deleted, who deleted it, and whether the action was successful.
The Script: Query "Delete Group" Audit Events with Graph PowerShell
# Connect to Microsoft Graph
Connect-MgGraph -Scopes "AuditLog.Read.All", "Directory.Read.All"
# Define time range - adjust as needed (last 7 days)
$startDate = (Get-Date).AddDays(-7).ToString("yyyy-MM-ddTHH:mm:ssZ")
$endDate = (Get-Date).ToString("yyyy-MM-ddTHH:mm:ssZ")
# Get 'Delete group' events under GroupManagement category
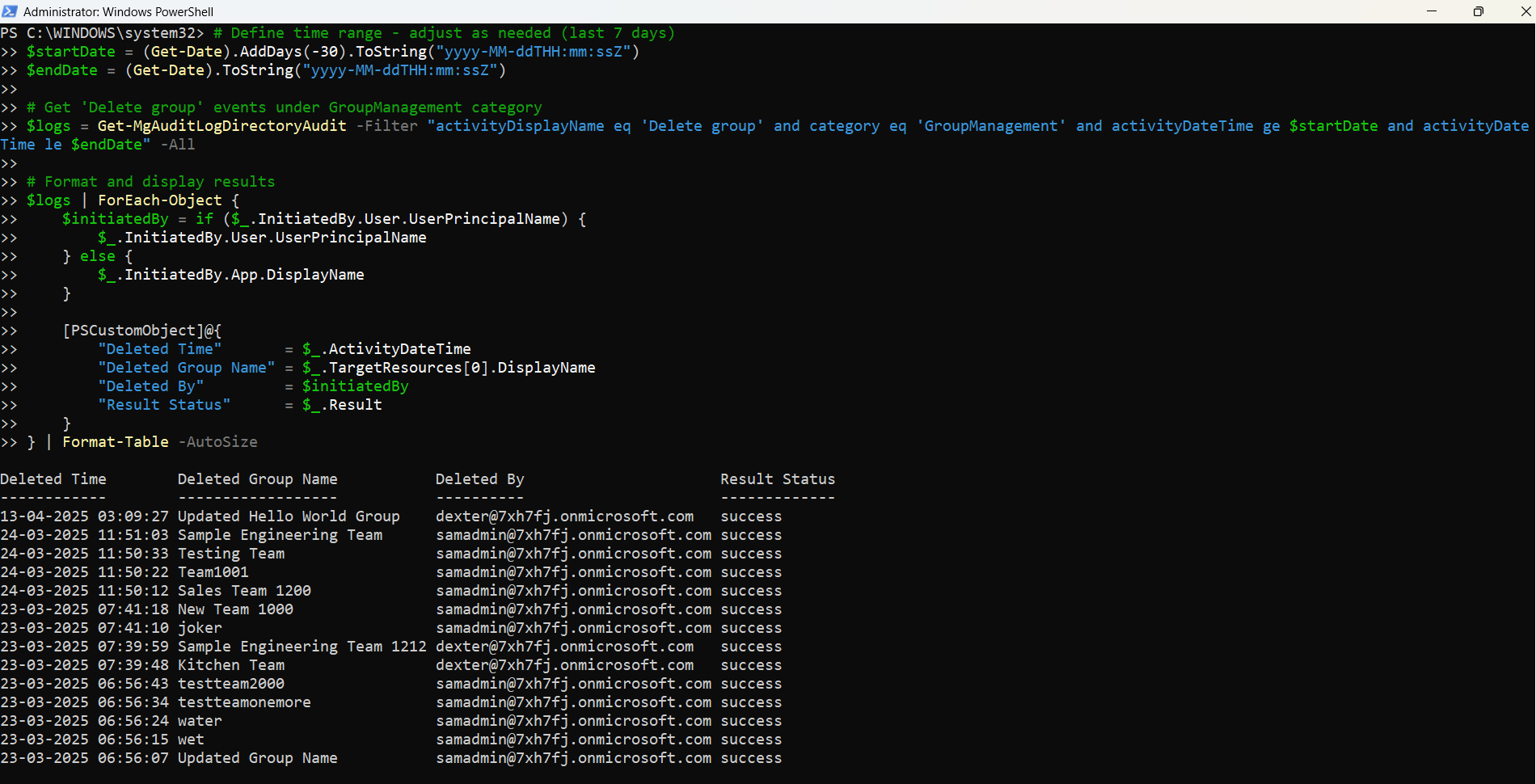
$logs = Get-MgAuditLogDirectoryAudit -Filter "activityDisplayName eq 'Delete group' and category eq 'GroupManagement' and activityDateTime ge $startDate and activityDateTime le $endDate" -All
# Format and display results
$logs | ForEach-Object {
$initiatedBy = if ($_.InitiatedBy.User.UserPrincipalName) {
$_.InitiatedBy.User.UserPrincipalName
} else {
$_.InitiatedBy.App.DisplayName
}
[PSCustomObject]@{
"Deleted Time" = $_.ActivityDateTime
"Deleted Group Name" = $_.TargetResources[0].DisplayName
"Deleted By" = $initiatedBy
"Result Status" = $_.Result
}
} | Format-Table -AutoSize
How the Script Works
Here’s how each part of the script functions:
- Connects to Microsoft Graph using the necessary permissions:
- AuditLog.Read.All (to access audit logs)
- Directory.Read.All (to read group data)
- Sets a date range for the logs. By default, it fetches logs from the last 7 days. You can adjust the $startDate and $endDate values as needed.
- Filters the logs where:
- activityDisplayName is "Delete group"
- category is "GroupManagement"
- activityDateTime falls within the specified range.
- Processes each log entry to extract and display:
- Deleted Time – when the deletion occurred
- Deleted Group Name – the name of the group that was deleted
- Deleted By – the UPN of the person who deleted the group, or the app name if deleted programmatically
- Result Status – success or failure
- Outputs the result using a clean table format for easy viewing.
Further Enhancements
Here are a few ways to extend and improve the script:
- Export to CSV for Reporting
- Make the Date Range Dynamic
- Include Additional Details
- Group ID:_.TargetResources[0].Id
- Correlation ID: _.CorrelationId
- Client IP Address: _.InitiatedBy.User.IpAddress (when available)
- Schedule the Script
- Windows Task Scheduler
- Azure Automation Runbooks
- Power Automate (via custom connector)
You can export the results for audit review or team reporting:
... | Export-Csv "DeletedGroupsAuditReport.csv" -NoTypeInformationInstead of hardcoding dates, allow user input:
$startDate = Read-Host "Enter start date (e.g. 2024-04-01)"
$endDate = Read-Host "Enter end date (e.g. 2024-04-10)"
This gives more flexibility during investigations.
You can enhance the output by adding:
These fields help in deeper investigation and correlation with other logs.
Make this part of a weekly or monthly compliance check by scheduling it through:
Possible Errors & Solutions
| Error | Cause | Solution |
| Insufficient privileges to complete the operation. | The signed-in user lacks the required Graph permissions. | Ensure you're connecting with AuditLog.Read.All and Directory.Read.All. Admin consent may be required. |
| TargetResources[0] is null | Some audit logs don’t carry resource data. | Add a null check before accessing properties to avoid runtime errors. |
| activityDateTime format is incorrect | Incorrect date format in the filter. | Use the ISO 8601 format like yyyy-MM-ddTHH:mm:ssZ, as shown in the script. |
| InitiatedBy is null or empty | Some events triggered by background services. | Fall back to InitiatedBy.App.DisplayName or use a default label. |
Conclusion
Tracking group deletions is crucial for security, transparency, and incident response. This Graph PowerShell script gives admins real-time visibility into who deleted what group and when, right from the console.
With just a few enhancements, this script can become a full-fledged reporting tool, integrated into your regular compliance workflows.