Track "Delete Application" Events Using Microsoft Graph PowerShell
Tracking deleted applications is crucial for maintaining the security and integrity of your Microsoft 365 environment. Using Microsoft Graph PowerShell, you can easily monitor "Delete application" events under the "ApplicationManagement" category. In this article, we'll provide a script to query these events, explain how the script works, suggest enhancements, cover use cases, highlight possible errors and their solutions, and wrap it all up with a conclusion.
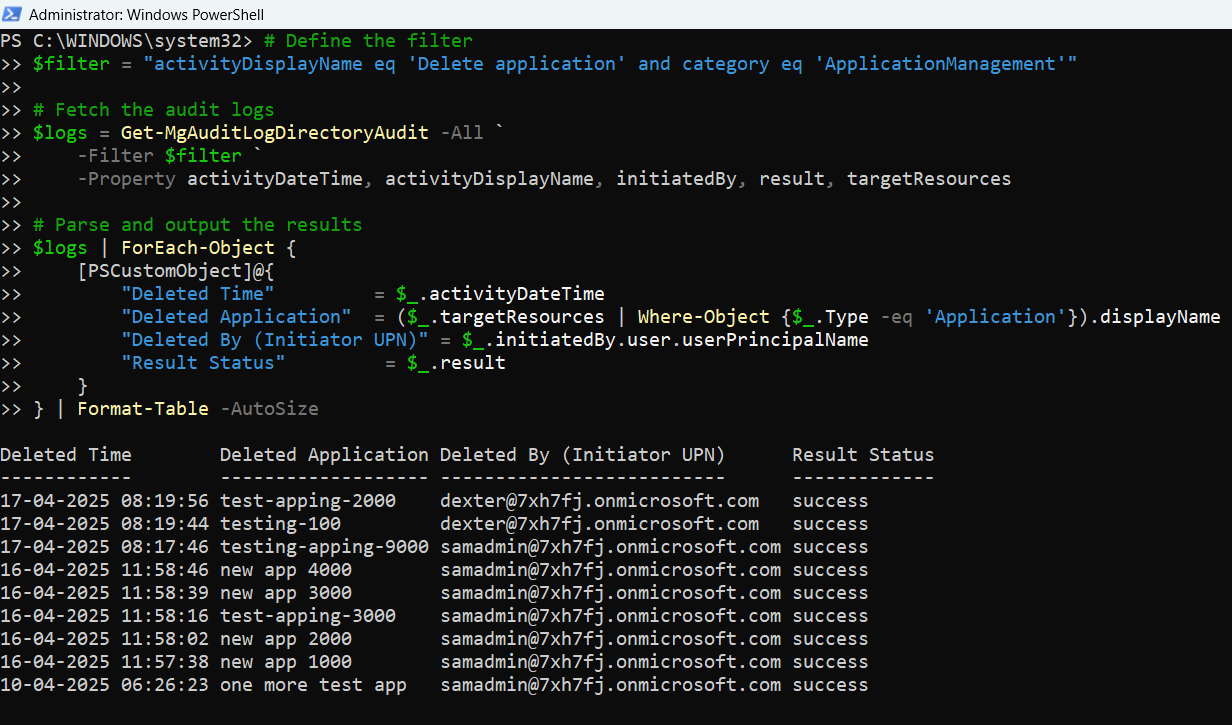
Script: Query "Delete Application" Events
# Connect to Microsoft Graph
Connect-MgGraph -Scopes AuditLog.Read.All
# Define the filter
$filter = "activityDisplayName eq 'Delete application' and category eq 'ApplicationManagement'"
# Fetch the audit logs
$logs = Get-MgAuditLogDirectoryAudit -All `
-Filter $filter `
-Property activityDateTime, activityDisplayName, initiatedBy, result, targetResources
# Parse and output the results
$logs | ForEach-Object {
[PSCustomObject]@{
"Deleted Time" = $_.activityDateTime
"Deleted Application" = ($_.targetResources | Where-Object {$_.Type -eq 'Application'}).displayName
"Deleted By (Initiator UPN)" = $_.initiatedBy.user.userPrincipalName
"Result Status" = $_.result
}
} | Format-Table -AutoSize
How the Script Works
- Authentication: The script connects to Microsoft Graph using AuditLog.Read.All permissions to access audit logs.
- Filter Creation: It defines a filter that specifically targets:
- activityDisplayName as "Delete application"
- category as "ApplicationManagement"
- Data Retrieval: It retrieves all audit logs that match the filter and pulls key properties like activityDateTime, initiatedBy, result, and targetResources.
- Data Processing: For each log entry:
- Deleted Time captures when the application was deleted.
- Deleted Application identifies the name of the deleted application.
- Deleted By (Initiator UPN) identifies the user who initiated the deletion.
- Result Status shows whether the deletion was successful or failed.
- Output: Results are displayed in a neatly formatted table in the console for quick review.
Further Enhancements
You can enhance this script by:
- Export to CSV: Save the output to a CSV file for audit trail purposes.
- Date Range Filter: Allow filtering by a specific date range to narrow down results.
- Error Handling: Add try-catch blocks to handle errors gracefully.
- Email Notifications: Send an alert email whenever a critical application is deleted.
- Scheduled Runs: Automate the script to run daily or weekly as part of a monitoring plan.
Use Cases
- Security Auditing: Identify unauthorized or accidental application deletions.
- Change Management: Maintain a log of deleted applications for compliance with internal change control processes.
- Incident Response: Investigate deletions during a security incident.
- Compliance Reporting: Provide evidence for audits by maintaining records of application deletions.
Possible Errors & Solutions
| Error | Cause | Solution |
| Insufficient privileges to complete the operation. | The user account lacks the necessary permissions. | Ensure you connect with an account that has the AuditLog.Read.All permission. |
| No audit records found. | No deletions match the filter or time period. | Verify that deletions occurred and adjust the timeframe if necessary. |
| Connect-MgGraph : Access token validation failure. | Session expired or incorrect tenant selected. | Re-run Connect-MgGraph and ensure correct tenant context. |
| Target resources array is empty. | No application resource linked to the event. | Add a fallback mechanism to handle missing target resources gracefully. |
Conclusion
Keeping track of deleted applications is vital for securing your Microsoft 365 environment and ensuring compliance. The provided Microsoft Graph PowerShell script offers a simple yet powerful way to monitor these critical events. With minor enhancements, such as automated reporting and alerting, you can build a comprehensive application governance and security framework. Regularly monitoring these activities helps prevent unauthorized actions and ensures that every change in your environment is tracked and accountable.