Track All User Events from Azure AD Audit Logs Using Graph PowerShell
Monitoring user-related events in Microsoft 365 is a critical part of maintaining security, compliance, and operational transparency. Whether you're tracking user creations, updates, deletions, or role changes, the Azure AD audit logs contain all the information you need. This article walks you through a Graph PowerShell script that fetches all user-related events and displays meaningful insights in your console.
The Script
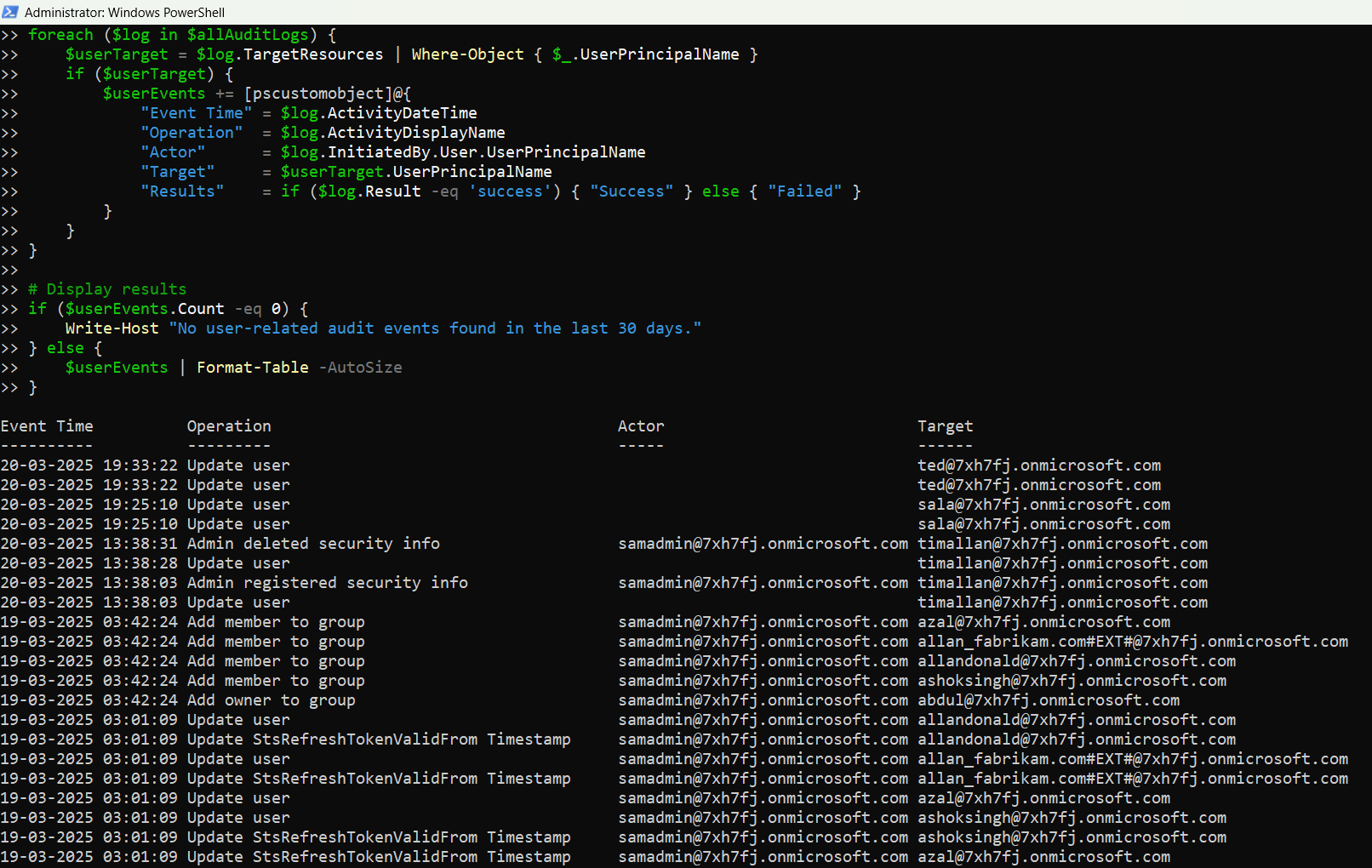
Here’s a Graph PowerShell script that fetches all Azure AD audit log entries where actions were performed on user accounts. It displays:
- Event Time
- Operation (e.g., Add, Update, Delete user)
- Actor (Who performed the action)
- Target (User affected)
- Result (Success or Failure)
# Connect to Microsoft Graph
Connect-MgGraph -Scopes "AuditLog.Read.All"
# Define timeframe (e.g., past 30 days)
$startDateTime = (Get-Date).AddDays(-30).ToString("yyyy-MM-ddTHH:mm:ssZ")
# Fetch all audit logs from the last 30 days
$allAuditLogs = Get-MgAuditLogDirectoryAudit -Filter "activityDateTime ge $startDateTime" -All
# Filter for logs where the target resource has a UserPrincipalName (indicating it's a user-related action)
$userEvents = @()
foreach ($log in $allAuditLogs) {
$userTarget = $log.TargetResources | Where-Object { $_.UserPrincipalName }
if ($userTarget) {
$userEvents += [pscustomobject]@{
"Event Time" = $log.ActivityDateTime
"Operation" = $log.ActivityDisplayName
"Actor" = $log.InitiatedBy.User.UserPrincipalName
"Target" = $userTarget.UserPrincipalName
"Results" = if ($log.Result -eq 'success') { "Success" } else { "Failed" }
}
}
}
# Display results
if ($userEvents.Count -eq 0) {
Write-Host "No user-related audit events found in the last 30 days."
} else {
$userEvents | Format-Table -AutoSize
}
How the Script Works
- Connects to Microsoft Graph using AuditLog.Read.All permission.
- Defines a 30-day date range to fetch logs using activityDateTime filter.
- Retrieves all directory audit logs within that period using Get-MgAuditLogDirectoryAudit.
- Loops through the logs and checks whether the event affected a user — based on the presence of UserPrincipalName in TargetResources.
- Builds a custom object with key audit details and displays them in a formatted table.
Further Enhancements
You can easily tweak this script to meet specific audit and reporting needs:
- Export Results to CSV:
$userEvents | Export-Csv -Path "UserEvents.csv" -NoTypeInformationWhere-Object { $_."Operation" -eq "Delete user" }$startDateTime = (Get-Date).AddDays(-90).ToString("yyyy-MM-ddTHH:mm:ssZ") # Last 90 days$userEvents | Sort-Object "Event Time" -Descending | Format-Table -AutoSizeUse Cases
This script is helpful in many day-to-day administrative scenarios:
- Security Audits: Track who deleted or modified user accounts.
- Compliance Reports: Document user-related events for auditors.
- Troubleshooting Access Issues: Understand recent changes made to user accounts.
- User Lifecycle Management: Monitor new user creations and removals.
- Admin Oversight: Keep tabs on which admins are performing critical changes.
Possible Errors & Solutions
| Error | Cause | Solution |
| Access Denied | Missing required permission | Connect using Connect-MgGraph -Scopes "AuditLog.Read.All" |
| The term 'Get-MgAuditLogDirectoryAudit' | Microsoft Graph module not installed | Install it using Install-Module Microsoft.Graph -Scope CurrentUser |
| No results found | No user events in the date range or incorrect filters | Widen the date range or remove overly specific filters |
Conclusion
Whether you're preparing for a compliance check, investigating changes to user accounts, or simply improving visibility, this Graph PowerShell script gives you a clear, customizable view of all user-related events in Azure AD audit logs.
With just a few lines of PowerShell, you can enhance transparency and accountability in your Microsoft 365 environment.
Try it out, adapt it to your needs, and never lose track of user activity again!