🔧 New: User Management Graph PowerShell Toolkit
Simplify user tasks like bulk creation, updates, password resets, deletions, license checks & more — all from one place.
🚀 Launch ToolkitTrack “Add Owner to Group” Event in Microsoft 365 Using Graph PowerShell
In Microsoft 365, group ownership controls who can manage membership, settings, and collaboration spaces like Teams. Adding owners to groups is a privileged operation—and tracking such changes is vital for auditing, security reviews, and compliance.
This article walks you through a Graph PowerShell script that queries audit logs for the “Add owner to group” event under the “GroupManagement” category and lists:
- Added Time
- Group Name
- Operation
- Added Owner (Target UPN)
- Added By (Actor UPN)
- Result
The Script: Fetch Group Owner Assignment Events with Details
# Connect to Microsoft Graph
Connect-MgGraph -Scopes "AuditLog.Read.All", "Group.Read.All"
# Define the audit log URI for "Add owner to group" events
$uri = "https://graph.microsoft.com/v1.0/auditLogs/directoryAudits" +
"?`$filter=activityDisplayName eq 'Add owner to group' and category eq 'GroupManagement'" +
"&`$orderby=activityDateTime desc"
# Fetch audit log events
$response = Invoke-MgGraphRequest -Method GET -Uri $uri
# Prepare result array
$results = @()
foreach ($entry in $response.value) {
try {
$addedTime = $entry.activityDateTime
$operation = $entry.activityDisplayName
$result = $entry.result
$actorUPN = $entry.initiatedBy.user.userPrincipalName
$groupId = ""
$groupName = ""
$addedOwnerUPN = ""
# Extract Group ID and User UPN from targetResources
foreach ($target in $entry.targetResources) {
if ($target.type -eq "Group" -and $target.id) {
$groupId = $target.id
}
if ($target.type -eq "User" -and $target.userPrincipalName) {
$addedOwnerUPN = $target.userPrincipalName
}
}
# If Group ID is available, fetch its display name
if ($groupId) {
try {
$group = Get-MgGroup -GroupId $groupId -Property DisplayName -ErrorAction Stop
$groupName = $group.DisplayName
} catch {
$groupName = "[Unknown Group]"
}
}
# Append the result
$results += [PSCustomObject]@{
'Added Time' = $addedTime
'Group Name' = $groupName
'Operation' = $operation
'Added Owner' = $addedOwnerUPN
'Added By' = $actorUPN
'Result' = $result
}
} catch {
Write-Warning "Error processing log entry: $($_)"
}
}
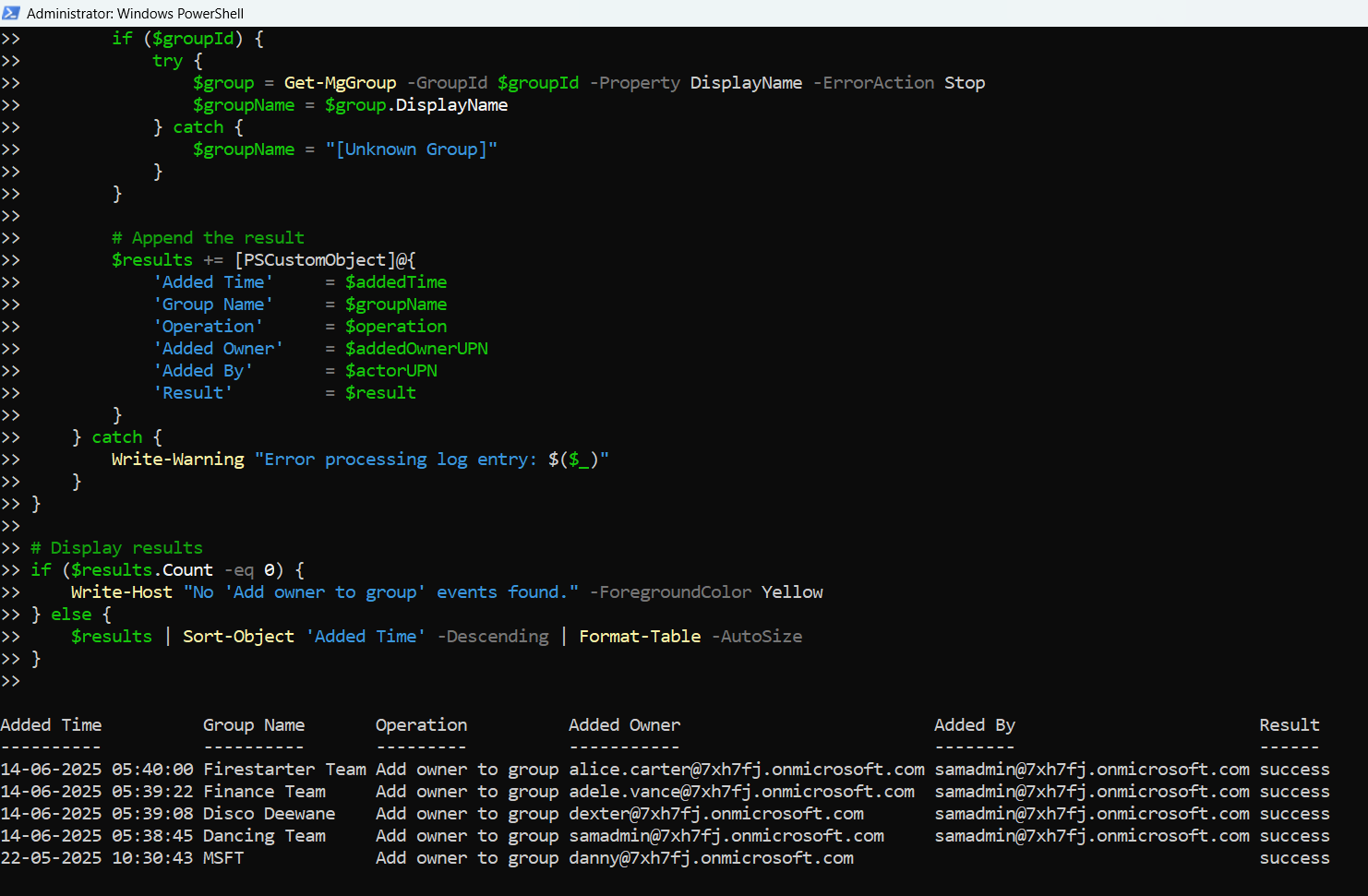
# Display results
if ($results.Count -eq 0) {
Write-Host "No 'Add owner to group' events found." -ForegroundColor Yellow
} else {
$results | Sort-Object 'Added Time' -Descending | Format-Table -AutoSize
}
How the Script Works
Required Permissions
You must connect with the following delegated permissions:
- AuditLog.Read.All – to access directory audit logs
- Group.Read.All – to resolve group display names from their IDs
Script Breakdown
- Connects to Microsoft Graph
- Queries the Audit Log
- Extracts Key Details
- Actor UPN (who performed the action)
- Target UPN (new group owner)
- Group ID
- Resolves Group Name
- Builds and Displays the Report
Uses Connect-MgGraph with proper scopes to authorize audit and group queries.
Filters events by:
activityDisplayName eq 'Add owner to group' and category eq 'GroupManagement'
This identifies all owner addition events across the tenant.
From each audit entry:
If only the Group ID is returned in the audit, the script uses Get-MgGroup to fetch its DisplayName.
Outputs a table with clear, readable values for auditing and compliance tracking.
Further Enhancements
Here are a few powerful ways to extend this script:
- Export to CSV
$results | Export-Csv -Path "GroupOwnerAudit.csv" -NoTypeInformationUse the $filter query to limit results to the past 30 days:
?$filter=activityDisplayName eq 'Add owner to group' and activityDateTime ge 2024-06-01T00:00:00ZNarrow down to specific users or service principals performing the operation.
Trigger alerts (e.g., via email) when new group owners are added.
Possible Errors & Solutions
| Error | Cause | Solution |
| Access Denied | Missing Graph scopes | Use AuditLog.Read.All and Group.Read.All when connecting |
| targetResources.userPrincipalName is null | The audit entry lacks UPN for user or group | Handle such entries with fallback or skip logic |
| Get-MgGroup : Resource not found | Group was deleted or soft-deleted | Wrap Get-MgGroup call in try/catch and use a placeholder label |
| Invoke-MgGraphRequest returns no results | No matching events found | Confirm recent activity in Entra audit logs or adjust filters |
Use Cases
This script has many practical applications:
- Security & Access Audits
- Compliance Reporting
- Troubleshooting & Investigations
- Admin Oversight
See who granted group ownership rights and to whom.
Provide clear audit trails for ownership changes.
Trace how a user became a group owner in sensitive contexts.
Monitor delegated authority in shared mailboxes, Teams, and Microsoft 365 Groups.
Conclusion
This Graph PowerShell script offers a powerful and reliable way to track group ownership changes in Microsoft 365. By leveraging the audit log and Graph API, you gain full visibility into who added group owners, when, and whether the operation succeeded.
Run this script regularly or integrate it into your admin toolset to ensure secure, auditable group management in your tenant.