Generate Self-Service Password Change Report Using Graph PowerShell
Monitoring self-service password changes helps IT admins validate user-initiated password updates and ensure users are actively managing their account security. Microsoft Graph PowerShell makes it easy to retrieve these events for auditing and compliance.
This article provides a step-by-step guide and script to generate a report for “Change password (self-service)” events using the Graph PowerShell SDK v1.0.
Script – Fetch Change Password (Self-Service) Events
# Connect to Microsoft Graph with required permission
Connect-MgGraph -Scopes "AuditLog.Read.All"
# Query Directory Audit Logs for "Change password (self-service)" events
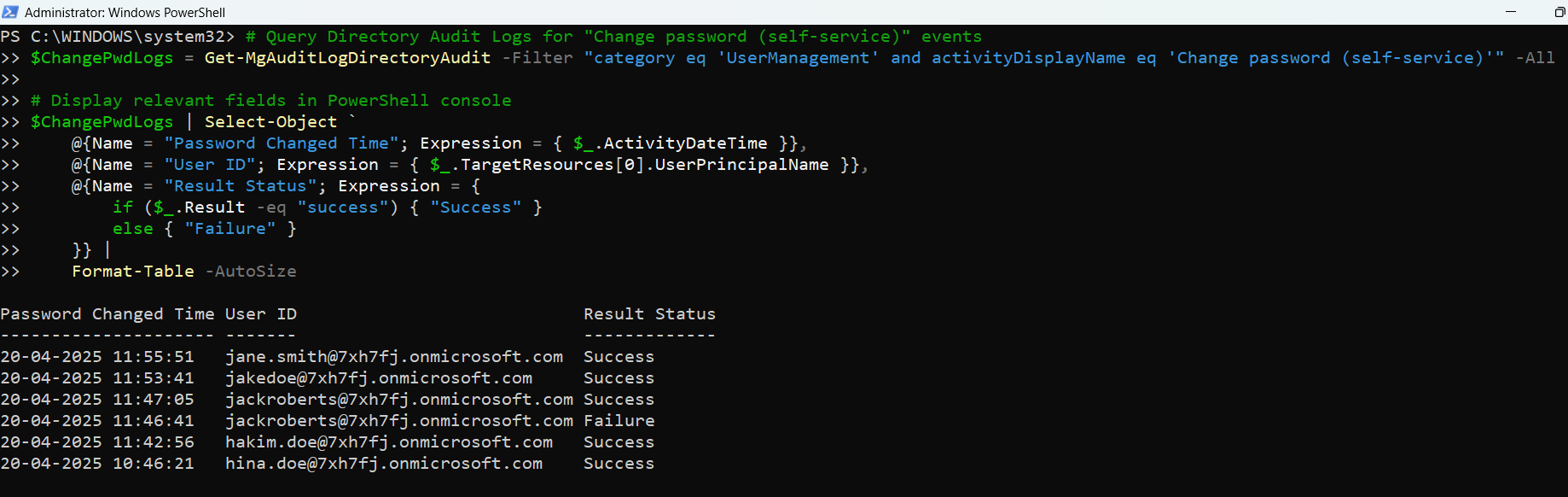
$ChangePwdLogs = Get-MgAuditLogDirectoryAudit -Filter "category eq 'UserManagement' and activityDisplayName eq 'Change password (self-service)'" -All
# Display relevant fields in PowerShell console
$ChangePwdLogs | Select-Object `
@{Name = "Password Changed Time"; Expression = { $_.ActivityDateTime }},
@{Name = "User ID"; Expression = { $_.TargetResources[0].UserPrincipalName }},
@{Name = "Result Status"; Expression = {
if ($_.Result -eq "success") { "Success" }
else { "Failure" }
}} |
Format-Table -AutoSize
How the Script Works
- Connection Setup: The script starts by connecting to Microsoft Graph using Connect-MgGraph and requests the AuditLog.Read.All permission scope.
- Event Filtering: The Get-MgAuditLogDirectoryAudit cmdlet is used with an OData filter:
- category eq 'UserManagement': Targets user-related activities.
- activityDisplayName eq 'Change password (self-service)': Fetches only self-service password change events.
- Data Extraction:
- ActivityDateTime: Time the password was changed.
- TargetResources[0].UserPrincipalName: Identifies the user who changed the password.
- Result: Displays whether the operation was successful.
- Output Formatting: Results are displayed as a clean table with appropriate headers.
Further Enhancements
Here are several improvements and extensions you can add to make the script more robust:
Filter by Date Range (e.g., Last 30 Days)
$$Since = (Get-Date).AddDays(-30)
$RecentPwdChanges = $ChangePwdLogs | Where-Object { $_.ActivityDateTime -ge $Since }
Export the Report to CSV
$ChangePwdLogs | Select-Object ... | Export-Csv -Path ".\SelfServicePwdChangeReport.csv" -NoTypeInformationCount Successful vs. Failed Attempts
To analyze success rates:
$ChangePwdLogs | Group-Object Result | Select Name, CountPossible Errors & Solutions
| Error Message | Cause | Solution |
| Connect-MgGraph is not recognized | Microsoft Graph SDK is not installed | Run Install-Module Microsoft.Graph -Scope CurrentUser |
| Insufficient privileges to call this API | Missing permission | Ensure the AuditLog.Read.All permission is granted and admin consent is provided |
| TargetResources[0] is null | Data inconsistency | Add null checks or skip incomplete records using Where-Object { $_.TargetResources } |
Use Cases
- Security Monitoring: Ensure users are actively managing their credentials.
- User Training Feedback: Evaluate how many users adopt self-service features after security training.
- Compliance Auditing: Maintain evidence of user-driven password changes.
- IT Helpdesk Optimization: Track the shift from helpdesk-dependent resets to self-service changes.
Conclusion
This PowerShell script using Microsoft Graph offers an efficient way to monitor and audit self-service password change events. Whether you're improving security posture, preparing for compliance audits, or analyzing user behavior, this report offers valuable insights with just a few lines of code.