Revoke-MgUserSignInSession: A Comprehensive Guide
Managing user sessions in Microsoft 365 is crucial for ensuring security and control over your organization's data. The Revoke-MgUserSignInSession cmdlet allows administrators to revoke active user sign-in sessions in Microsoft 365, forcing reauthentication. This guide explores the syntax, examples, tips, use cases, possible errors, and solutions to help you effectively use this cmdlet.
Cmdlet Syntax
Revoke-MgUserSignInSession -UserId <String>Parameters:
- -UserId: Specifies the unique identifier or User Principal Name (UPN) of the user whose sessions are to be revoked. This parameter is required.
Usage Examples
Example 1: Prompting Admin for User Input
You'll be prompted to enter or pass the UserId or UPN if you use the cmdlet directly. The user session is revoked when you pass the UserID or UPN.
Revoke-MgUserSignInSession 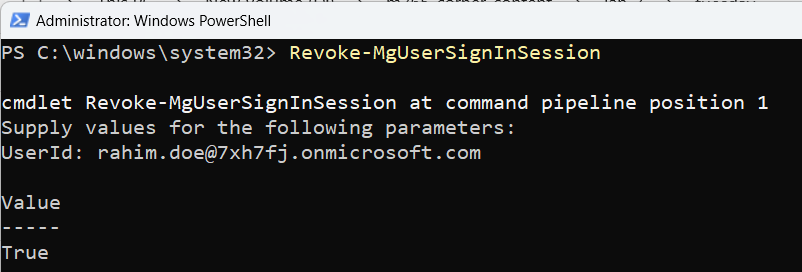
Example 2: Directly Passing the User ID
This example shows how to revoke a user’s session by directly passing their ID or UPN to the cmdlet.
# Revoke sessions for a specific user
Revoke-MgUserSignInSession -UserId "user@example.com"
Cmdlet Tips
- Use Secure Input: If you’re dealing with sensitive environments, use
Read-Host -AsSecureStringto avoid displaying input in plaintext. - Monitor Sign-In Activity: Combine this cmdlet with
Get-MgUserSignInActivityto identify users with suspicious login activity before revoking sessions. - Admin Consent: Ensure you have appropriate permissions, such as the
User.ReadWrite.Allpermission, to execute this cmdlet. - Immediate Effect: Revoking sessions forces users to reauthenticate immediately, so communicate with affected users beforehand if possible.
Use Cases
- Responding to Security Incidents: Revoke sessions for a user whose account is suspected of being compromised.
- Enforcing MFA: Ensure users reauthenticate after enabling multi-factor authentication (MFA) for their accounts.
- Terminating User Access: Revoke access for users who are leaving the organization to ensure no further access to company resources.
Frequently Asked Questions
- Does Revoke-MgUserSignInSession immediately sign the user out from all devices?
- How can I verify if a sign-in session was revoked successfully?
- Will this cmdlet revoke sessions for service principals or app registrations?
- Does revoking a user’s session also reset their password?
- Can revoked sessions still allow offline access to cached data?
No, it only invalidates the user's refresh tokens. Existing access tokens remain valid until they expire, so the user may not be signed out immediately.
The cmdlet does not return output. To verify, check Azure AD audit logs or track changes in sign-in behavior using Get-MgAuditLogSignIn.
No, Revoke-MgUserSignInSession is intended for user accounts only, not for applications or service principals.
No. Revoking sign-in sessions only invalidates refresh tokens and forces reauthentication. The user’s existing password remains valid unless explicitly reset using Update-MgUser or other password reset methods.
Yes, in some cases. If applications cache data locally (for example, Outlook OST files or Teams offline files), users may still see previously synced content. Revoking sessions only blocks future authentication and access to cloud resources.
Possible Errors & Solutions
| Error | Cause | Solution |
| Insufficient privileges to complete the operation | The admin account lacks the required permissions | Assign the User.ReadWrite.All permission to your account or role. |
| Invalid user ID or UPN provided | The -UserId parameter value is incorrect or does not exist in your tenant. |
Verify the user ID or UPN using the Get-MgUser cmdlet:
|
| Resource not found | The user specified by the -UserId does not exist |
Double-check the ID or UPN for typos and ensure the user exists in the tenant. |
Revoking Tokens Doesn’t Immediately Log Out the User
Revoke-MgUserSignInSession, users may still retain access for a short time until the current tokens expire. This cmdlet invalidates refresh tokens, but existing access tokens remain valid until their expiry.
No Output Is Expected After Successful Execution
Revoke-MgUserSignInSession cmdlet does not return any output upon success. To confirm revocation, check audit logs or monitor recent user sign-ins using Get-MgAuditLogSignIn.
Revoke-MgUserSignInSession terminates all active refresh tokens for the user — across browsers, mobile apps, and desktop clients.
This ensures sign-ins are invalidated everywhere, forcing the user to reauthenticate before accessing Microsoft 365 resources again.
Conclusion
The Revoke-MgUserSignInSession cmdlet is a powerful tool for managing Microsoft 365 user sessions. Whether you’re responding to a security incident or enforcing new policies, this cmdlet provides administrators with a straightforward way to revoke access and enhance security. By understanding its syntax, usage, and potential pitfalls, you can effectively utilize this cmdlet to protect your organization’s resources.