Monitor Forced Password Change Flags Using Graph PowerShell
In Microsoft 365 environments, administrators may enforce a policy that forces users to change their password at the next login. This is a common security control used when:
- An account is suspected of compromise,
- A user joins the organization,
- Or during periodic password hygiene enforcement.
When this setting is toggled, Azure AD logs an audit event called “Update PasswordProfile” under the “UserManagement” category. This event is distinct from actual password resets — it captures the enforcement of the “must change password on next login” requirement.
In this article, you'll learn how to use Graph PowerShell to query and display these security-driven admin actions in a clean and readable format.
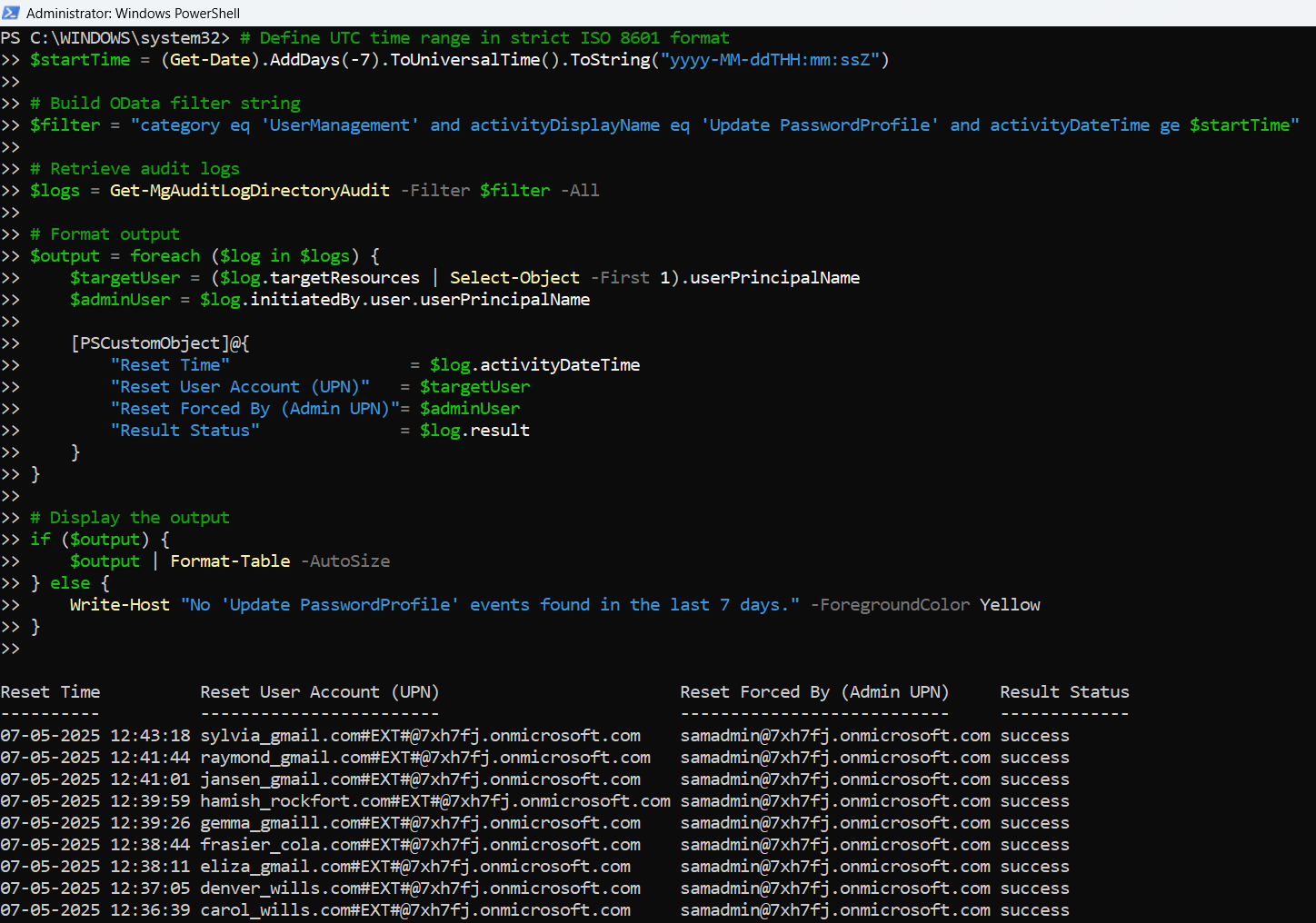
The Script: Querying "Update PasswordProfile" Events
# Connect to Microsoft Graph
Connect-MgGraph -Scopes "AuditLog.Read.All"
# Define UTC time range in strict ISO 8601 format
$startTime = (Get-Date).AddDays(-7).ToUniversalTime().ToString("yyyy-MM-ddTHH:mm:ssZ")
# Build OData filter string
$filter = "category eq 'UserManagement' and activityDisplayName eq 'Update PasswordProfile' and activityDateTime ge $startTime"
# Retrieve audit logs
$logs = Get-MgAuditLogDirectoryAudit -Filter $filter -All
# Format output
$output = foreach ($log in $logs) {
$targetUser = ($log.targetResources | Select-Object -First 1).userPrincipalName
$adminUser = $log.initiatedBy.user.userPrincipalName
[PSCustomObject]@{
"Reset Time" = $log.activityDateTime
"Reset User Account (UPN)" = $targetUser
"Reset Forced By (Admin UPN)"= $adminUser
"Result Status" = $log.result
}
}
# Display the output
if ($output) {
$output | Format-Table -AutoSize
} else {
Write-Host "No 'Update PasswordProfile' events found in the last 7 days." -ForegroundColor Yellow
}
How the Script Works
- Authentication :
- It starts by connecting to Microsoft Graph with the required AuditLog.Read.All scope.
- Event Filtering:
- It specifically looks for audit logs with:
- category eq 'UserManagement'
- activityDisplayName eq 'Update PasswordProfile'
- Entries recorded in the last 7 days.
- Extracting Useful Information:
- For each matching event, it retrieves:
- The timestamp (Reset Time)
- The affected user (Reset User Account (UPN))
- The admin who triggered the action (Reset Forced By (Admin UPN))
- The operation result (Success or Failure)
- Output Formatting:
- Results are displayed neatly using Format-Table.
Understanding the Event
The "Update PasswordProfile" event does not track regular password resets. Instead, it logs a specific administrative action:
When an admin enforces a password change at next sign-in by toggling the forceChangePasswordNextSignIn flag for a user.
This is commonly done for:
- New employees,
- Suspicious accounts,
- Or post-reset security policy compliance.
It's a preventive or reactive security control, not a reset log.
Further Enhancements
You can customize the script as needed:
- Export to CSV
$output | Export-Csv -Path "ForcedPasswordChangeAudit.csv" -NoTypeInformation$output | Where-Object { $_."Reset Forced By (Admin UPN)" -like "*securityadmin@" }(Get-Date).AddDays(-30)Possible Errors & Solutions
| Error | Cause | Solution |
| Invalid filter clause | Incorrect DateTime format | Use ToUniversalTime().ToString("yyyy-MM-ddTHH:mm:ssZ") |
| Access Denied | Missing permissions | Ensure AuditLog.Read.All is granted and consented |
| Parameter not found | Using unsupported params | Don’t use -ConsistencyLevel, -Property, etc. |
Use Cases
- Security enforcement tracking: Monitor when admins are requiring users to reset passwords as part of protocol.
- Onboarding audits: Confirm that new users are set to change their password on first login.
- Compromise response: Check which accounts were flagged for forced password change due to suspected breach.
- Compliance and alerting: Feed this into SIEM tools or send notifications to security teams.
Conclusion
The Update PasswordProfile audit event offers valuable visibility into admin-triggered password change requirements, especially in environments where password hygiene and account integrity are paramount.
With the help of Graph PowerShell, you can extract these entries, review the actions taken, and build automated alerting or auditing solutions to maintain compliance and security awareness across your Microsoft 365 tenant.